Recommended Practices: Dealing with CryptoLocker
This is a multi-part series on recommended IT practices for organizations and their end-users. Additional parts will be included in upcoming newsletters.
CryptoLocker surfaced in the fall of 2013; it is a ransomware trojan that, upon activation, encrypts all data files to which the infected end-user has read-write access, and then demands payment to decrypt. It typically hides as an attachment within a phishing email and can even work over a home user’s VPN connection to encrypt data files on the organizations’ server(s).
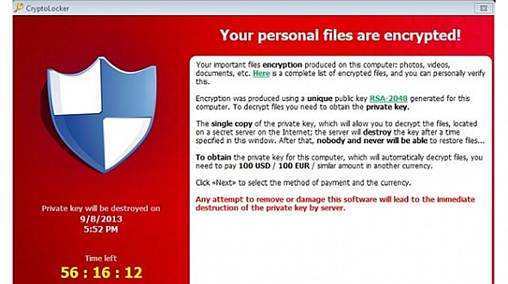
The cyber-criminal’s intent is to receive untraceable payment via cyber-currency in exchange for a decryption key to unlock the data files, forming a one-to-one relationship between the cyber-criminal and the infected user: The cyber-criminal knows the user is infected and awaits payment; if thwarted in his/her extortion attempt, that information is retained by the cyber-criminal, which could reduce future efforts to pursue your organization.
Of greater concern; if an individual or organization pays the ransom, that information is also known, recorded, and potentially shared for future attempts. Basically, if you pay the ransom, you may be targeted for new efforts.
The cyber-criminal is likely acting within a crime syndicate; he/she might not even be technically savvy since CryptoLocker tools are readily available and easy to use.
We have recently seen a significant upswing in CryptoLocker attempts; the source emails spoof the email addresses of known parties while the attachment might carry a seemingly harmless “PDF” extension. The message is compelling; an end-user unwittingly clicks the attachment and starts the process.
The first best step is prevention:
- If feasible, use group policies or AppLocker to restrict software execution1
- Limit access only to needed files; make them read-only where appropriate
- Update security patches on all operating systems and end-user applications2
- Deploy and continually update anti-malware apps on all end-user devices2
- Deploy a robust, anti-spam solution that can block executables2
- Consider blocking or quarantining all incoming attachments
- Setup a backup routine that addresses data files frequently3
For more information, Jonathan Haskell of ComputerWorld reviews group policy restrictions in his article: “CryptoLocker: How to avoid getting infected and what to do if you are”. Also, Third Tier and SMB Kitchen have jointly released a CryptoLocker Prevention Kit to assist in developing these group policies.
Education is also critical4:
- Schedule regular training reviews with your end-users
- Demonstrate to your end-users how to spot potential threats
- Discuss the dangers of clicking attachments, even those from known sources
If you are infected by CryptoLocker5:
- Identify the infected computer and remove it from the network
- To be prudent, change online and system passwords
- Create forensic images of infected computers
- Preserve all firewall, Intrusion Prevention, and Active Directory logs for potential analysis by law-enforcement officials
Index of referenced articles:
1 See the January 2015 Bryley Tips and Information article: Recommended Practices: Manage End Users via Active Directory and the February issue for the article: Recommended Practices – Part 7: Resource Management via Active Directory.
2 See the June 2015 Bryley Tips and Information article: Recommended Practices: IT security cheat-sheet.
3 See the April issue of Bryley Tips and Information for Bryley Basics: How ransomware (CryptoLocker) makes backups more critical.
4 See the May 2015 Bryley Tips and Information article: Recommended Practices: Basic IT training for end users
5 View detailed prevention and response techniques in CryptoLocker Prevention and Remediation Techniques, presented by fishnet™ security.








