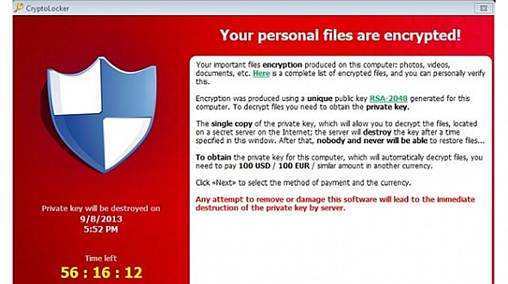
Bryley Basics: Critical steps before opening an unknown attachment or a link
Since Ransomware and other malware often travel as attachments or web-links, Anna Darlagiannis, Manager of Client Relationships, offers these tips:
1. Don’t open an email or attachment or click on a link within an email if you don’t know who sent it to you….period!
2. Check and see who the email was actually sent to.
If the email was sent to a distribution list, then be especially vigilant before opening it. For example, hackers can assume that a company’s accounts payable distribution email address is accountspayable@companydomain.com or any other variations such as AP@companydomain.com or accounts-payable@companydomain.com. Hackers recognize that accounts payable departments anticipate attachments marked “invoice” or “PO” or other related keyword(s) and will name the attachment accordingly. Furthermore, distribution lists are typically posted on a company’s website making these email addresses public knowledge and easy targets.
Tip: Setup rules within Outlook to have emails that are sent to a distribution list automatically move into a specified folder(s). This will make it easier to know exactly what email address was used to send you the email.
NOTE: It is NOT safe to assume that all email attachments and/or links sent to your personal email address are safe to open.

3. Check who sent you the email.
Hackers can spoof a name, but they can’t spoof an email address. The email may be marked with a familiar name, prompting you to open the email and/or attachment/link, but if you pay close attention to the actual email address, you may be surprised. (Unfamiliar email addresses should never be opened.) For example, your boss’s name is John Smith and his email address is JSmith@companydomain.com. You receive an email that is marked “From: John Smith” and assume this came from your boss. You go to open the email and find an attachment. At this point, you must also look at the actual email address before opening the attachment. If the email address isn’t JSmith@companydomain.com, then delete it and/or block the domain with your SPAM filter immediately and make everyone in the organization aware of what is going on.
If the email address is correct, but the attachment/link/signature/way that the person writes an email looks suspicious, be cautious, call the person that sent you the email (do not email in case the email address is compromised) and ask if what they sent you was in fact legitimate.

4. Scan the attachment with your anti-virus program before opening.
Take the attachment from the email and drag it to your desktop. From there, right click on the attachment and then scan it using your anti-virus program. Be sure to update the anti-virus program prior to scanning it, to ensure that you have the latest updates applied to the anti-virus program.
Unfortunately, this approach isn’t full proof. An anti-virus program may not recognize all viruses, especially if they are newly created viruses.